# Description
OS command injection vulnerability found in SQLS version 0.2.28 in the openEditor() function in main.go. The openEditor() function constructs and executes the contents of the EDITOR environment variable by invoking a system shell (sh -c on POSIX or cmd /c on Windows) rather than executing a program with discrete arguments. An authenticated user (or attacker) can change the EDITOR value may cause arbitrary commands to be executed with the same privileges as the SQLS process (i.e., the privileges of the user or service account that runs the SQLS binary).
# Proof of Concept
Youtube Link: https://www.youtube.com/watch?v=ODGAOuLe-A4
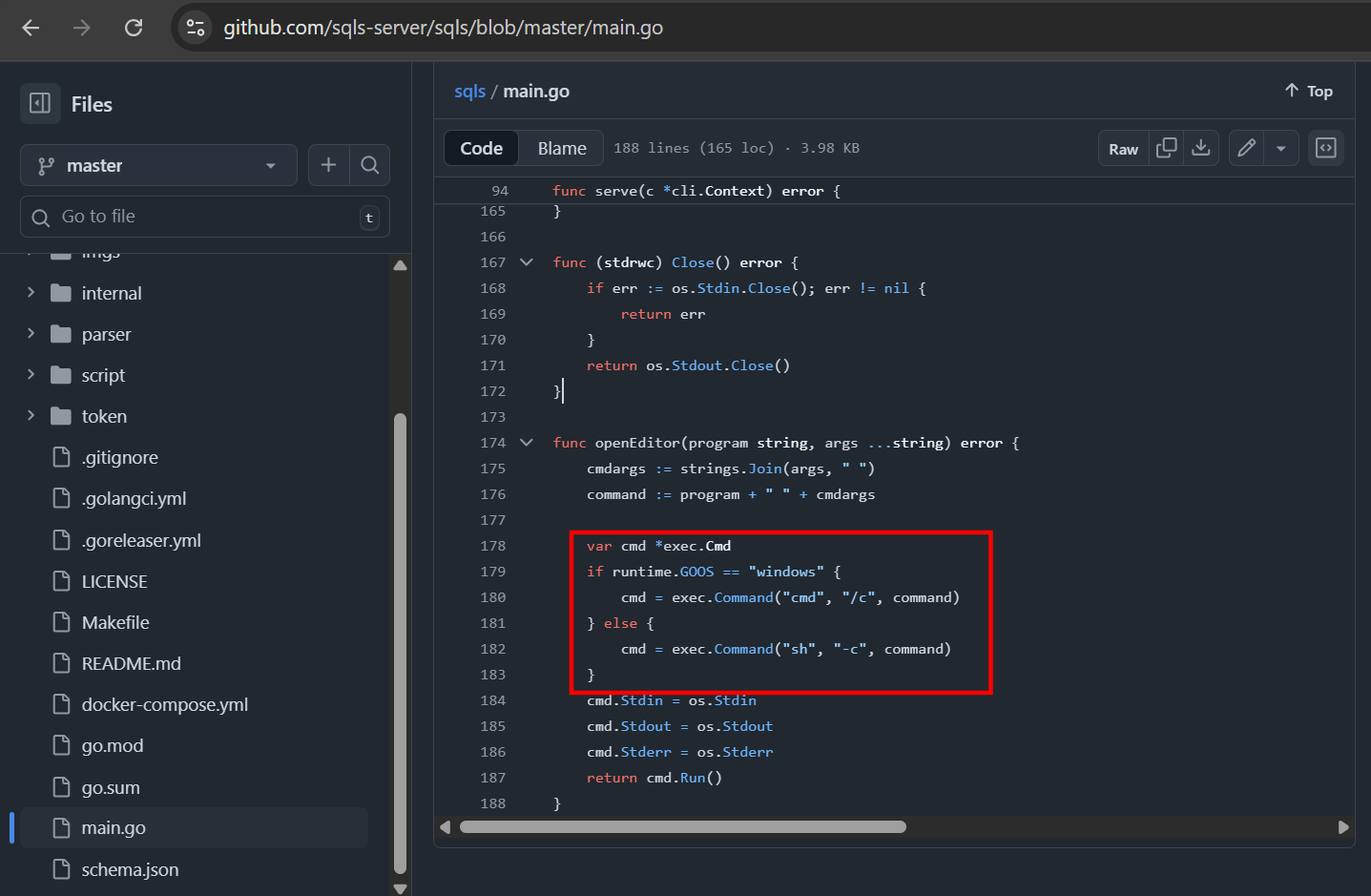
The openEditor() function uses exec.Command("sh", "-c", ...) without sanitized input, which spawns a POSIX shell to parse and execute the entire command string (including pipes, redirects, globbing, etc.), enabling OS command injection.
func openEditor(program string, args ...string) error {
cmdargs := strings.Join(args, " ")
command := program + " " + cmdargs
var cmd *exec.Cmd
if runtime.GOOS == "windows" {
cmd = exec.Command("cmd", "/c", command)
} else {
cmd = exec.Command("sh", "-c", command)
}
cmd.Stdin = os.Stdin
cmd.Stdout = os.Stdout
cmd.Stderr = os.Stderr
return cmd.Run()
}
exec.Command("sh", "-c", command)
# Impact
This issue lead to a arbitrary command execution.
# CVSS4.0 and CWE
7.0 / High CVSS:4.0/AV:L/AC:L/AT:N/PR:H/UI:A/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N
CWE-20: Improper Input Validation
CWE-78: Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection')
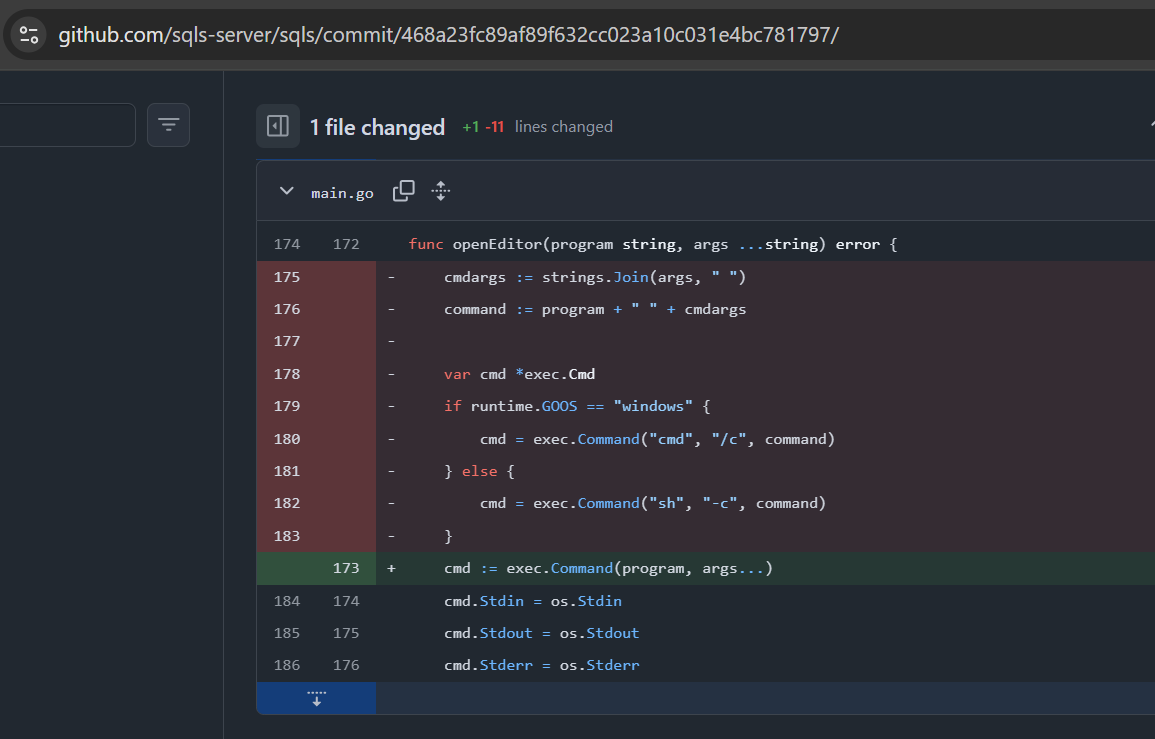
# Vulnerability Fixed
# Timeline
- 6 Sept 2025 >> Submit CVE at https://cveform.mitre.org/
- 25 Oct 2025 >> Got email for reserved CVE-2025-61141
- 29 Oct 2025 >> This POC
- 30 Oct 2025 >> Vulnerability Fixed: https://github.com/sqls-server/sqls/commit/468a23fc89af89f632cc023a10c031e4bc781797/